Common attack vectors for authentication service
This guide gives an overview of common security issues when building authentication services for computer systems and best practices to mitigate them.


Ory Guest
Hacking user accounts on many websites is still easier than it could and should be. This blog post helps you secure your application against identity theft by going over the most common hacker attacks against authentication services and outlining mitigations against them.
Password guessing
One of the easiest ways to steal someone's account is to try all possible passwords until one of them works. This is called a brute-force attack. At first, there seem to be many possible passwords one would need to try here. However, password guessing attacks are more successful than one might assume because many people use similar passwords. Here is a list of the most common ones. If your password is listed here, anybody in the world can hack your account in a few minutes by just trying these passwords manually! More sophisticated hackers use computer scripts to try millions of passwords per second, for example, all words in the dictionary, possible combinations of words and numbers, and the list keeps increasing.
You can protect your application against password guessing by making the passwords harder to guess: longer (at least 8 characters) and with a wider variety of symbols. Another effective mitigation is waiting some time after encountering an incorrect password, ideally longer with each successive failed attempt (exponential backoff). This slows automated scripts down to levels where they can never try a large number of passwords. Finally, check your users' passwords against databases of leaked passwords that are known to hackers, for example haveibeenpwned.
Hackers often get access to your database and read all its contents. If you store your users' passwords in clear text there, the hacker will know the passwords of all your users among other important details. Avoid this by keeping only a fingerprint (hash) of passwords in your database. When a user enters a password during login, you create a fingerprint of that password and compare it to the one you have on file. If the fingerprints match, the passwords must match as well.
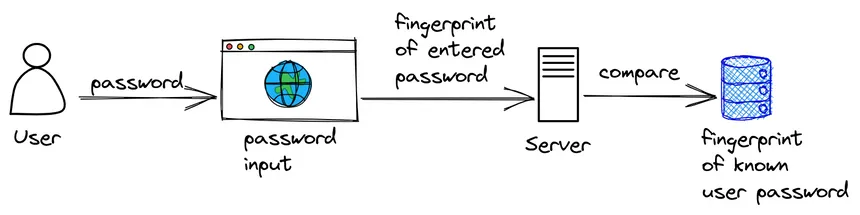
Choose a strong hashing algorithm like bcrypt/Argon2. Hackers can reverse-engineer simple fingerprints using rainbow tables. Mix the fingerprints with a random element called salt to prevent this.
The best passwords are complete random characters. Password managers like 1password or bitwarden help create and store them.
Key takeaways:
- Ensure sufficient entropy in your users' passwords to make them hard to guess.
- Ensure your users don't use leaked passwords.
- Use a gradually increasing delay between unsuccessful authentication attempts to avoid password guessing.
- Use a strong hashing algorithm with salt.
- Use a password manager to create and manage unique passwords for each service.
If all that sounds too complicated, give Ory Kratos a try because it implements all of these best practices out of the box.
Data interception attacks
Even the best password isn't good enough if an attacker can observe the user entering it. This can happen when bystanders watch your keyboard while you enter your password. It is, therefore, a part of good etiquette to look away when others enter their passwords. Your password can also be seen by others when it is sent over via un-encrypted wireless connections like FTP or unencrypted WiFi.
Protect yourself against these attacks by always using encrypted network connections like SSL, SFTP, and HTTPS, instead of FTP and HTTP. Make sure to use modern versions since some older SSL versions are not secure anymore.
Key takeaways:
- Use SSL everywhere and periodically audit the setup.
- Configure SSL with HSTS and Certificate Transparency.
Spyware
An encrypted connection doesn't help if the computer through which the user enters the password contains hidden spyware that sends all entered text, the screen content, or your website cookies to the hacker. Hackers can efficiently scan large amounts of captured keystrokes for text that looks like passwords, credit card numbers, social security numbers, and other valuable data. Stolen cookies allow an attacker to make requests look like they're coming from you.
Secure yourself against malware by installing all software updates, using a modern web browser, avoiding shady websites and software, and running anti-virus software. You can reduce cookie leaks by making the lifetime of cookies short. That's why Ory Kratos limits the lifetime of cookies to one hour.
With two-factor authentication, a user enters their username and password to authenticate, and then they are required to provide another aspect to identify themselves. This second aspect could be a time-based one-time-password or a code sent via text message to your phone, although the latter is less secure. Two-factor authentication helps against stolen passwords and spyware since the second factor is always different.
Takeaways:
- Bind a cookie to a user's IP address.
- Use a short cookie lifetime.
- Always install all software updates.
- Use anti-virus software.
- Use a modern web browser.
- Enable two-factor authentication.
- Use CSRF tokens on authentication forms to avoid "Connect" request interception.
- Consider using WebAuthn for passwordless flows in browser.
Social engineering and phishing attacks
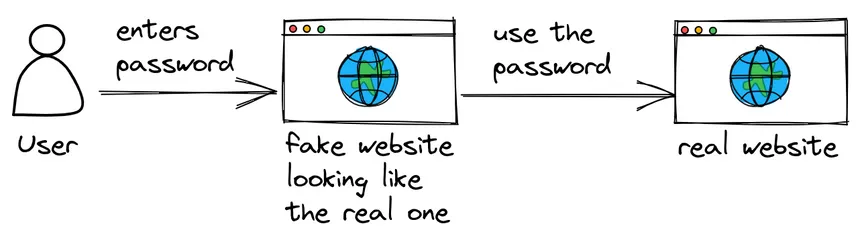
The weakest link in your security architecture are the human users. The best passwords aren't secure if people are tricked into revealing them to an attacker as part of social engineering. You find many examples of social engineering in the movie Takedown. Here is an example that combines social engineering with a man-in-the-middle attack:
George uses Gmail with 2-factor-authentication. Andrew wants to read George's
emails but doesn't have the password. To get it, Andrew creates a website that
looks exactly like Gmail's login screen, with a URL that sounds very close to
it, like gmoil.com. Sophisticated hackers can also use a
DNS poison attack
to make their fake website appear as gmail.com. To make George use this fake
website, Andrew sends him a fake advertisement claiming that George won a free
Gmail upgrade and just needs to log in to activate it. When George clicks on the
link in the fake ad, he ends up at Andrew's fake login page and enters his Gmail
username and password. Andrew sees the credentials and enters them into the real
Gmail website. George then enters the code received on his phone into Andrews
fake website, which Andrew also enters into the real Gmail. Andrew is now logged
into George's email. The fake website shows an error message and tells George
that there was an error and he should try again, then redirects him to the real
Gmail website. George logs in again and everything works this time. George
doesn't think much of it and goes on with his day.
Further reading

The future of Identity: How Ory and Cockroach Labs are building infrastructure for agentic AI

Ory and Cockroach Labs announce partnership to deliver the distributed identity and access management infrastructure required for modern identity needs and securing AI agents at global scale.

Ory + MCP: How to secure your MCP servers with OAuth2.1

Learn how to implement secure MCP servers with Ory and OAuth 2.1 in this step-by-step guide. Protect your AI agents against unauthorized access while enabling standardized interactions.