Login and authentication in 2023 explained — Passkeys, Google Authenticator, TouchID
How should you and your customers log in, in 2023? This in-depth guide explains it all.


Founder & CTO
How should my users log into my SaaS app? What should be the password requirements? What sign-up methods should I offer? Are Passkeys the end of passwords?
Answering these questions requires experience and research, like with any computer science topic. In this article, I’ll try my best to help you make the right decision for your company and threat model.
I believe that my opinion is worth publishing, as I have been working in this space for over a decade and have implemented all of the mentioned methods in Ory’s popular open-source projects from design to production. Through this experience, I worked with authentication methods in many real-world scenarios and encountered the challenges each of them comes with. In this article, we will explore all the different authentication methods available today, including their benefits and drawbacks, and discuss how and if they can provide a higher level of security than traditional password-based authentication.
Passwords are … dead?

The way we log in to websites and online accounts has evolved significantly over the past few years. Passwords have long been the primary method of authentication for online accounts, but in recent years, they have fallen out of fashion due to their vulnerability to cyber-attacks.
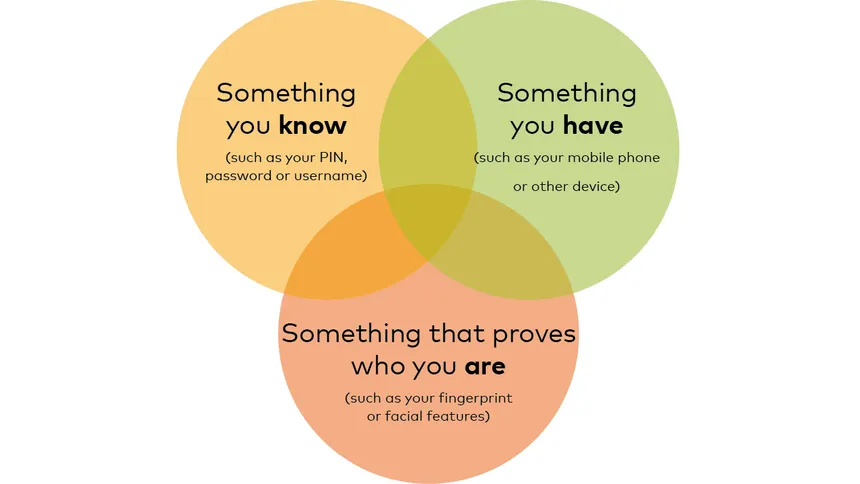
Today, we have access to a wide range of authentication methods that use various factors to verify our identity. These factors can be categorized into three main types: something you are, something you have, and something you know.
But is the password truly dead, or just one out of three imperfect solutions each with its own set of tradeoffs?
There is no perfect authentication factor
Let’s take a closer look at the three types of authentication factors: something you are, something you have, and something you know. We will discuss the benefits and drawbacks of each factor and provide examples of authentication methods that use each factor.
Something you are … has false positives
Something you are **usually refers to biometric authentication, which uses unique physical characteristics such as fingerprints, facial recognition, or iris scans. It can be a great way to prevent password-related attacks such as credentials stuffing, dictionary attacks, and phishing. Since biometric data is unique to each individual, it is much more difficult for an attacker to obtain and replicate this data than it is to obtain a password.
This makes it much harder for attackers to gain access to a system using stolen or hacked passwords. However, biometric authentication is not without its drawbacks.
Biometric authentication is based on statistics, which means that there is a chance of false positives and false negatives. False positives occur when a user is incorrectly authenticated, while false negatives occur when a user is not recognized. For example, a user may have difficulty using Touch ID on their device after swimming or washing their hands, as the water can change the shape of their fingerprints, leading to false negatives. Biometric authentication should be used with other non-biometric authentication methods to ensure the highest level of security.
| True | False | |
|---|---|---|
| Positive | Logged in | Security incident |
| Negative | Login Rejected | Not able to sign in |
The National Institute of Standards and Technology (NIST) has a great blog article titled "A Tale of Two Errors: Measuring Biometric Algorithms." It provides a detailed explanation of false positives and false negatives in biometric authentication and how they can be measured and addressed.
Fingerprints can easily be copied for low cost and any device (e.g. phone or laptop) has thousands of fingerprints on it. Physical access to a device thus may give you access to fingerprints, too.
Something you have … can be stolen
Something you have is a physical device like a smart card or USB key that can be used to verify your identity. It is another effective way to protect against password-based attacks.
However, while it provides a high level of security when in your possession, it can provide a very low level of security if stolen. For instance, with RFID and NFC readers/emulators like the Flipper Zero, it can be trivial to copy a keycard. Similarly, if a YubiKey 5 is stolen and no pin code is set, an attacker can use it without any additional authentication. Therefore, it's important to combine something you have with another factor to increase the security level. By using multiple factors, an attacker would need to have access to both the physical token and another factor such as a password, making it much harder to gain access to a system.
Something you know … can be guessed
Something you know, such as a password or PIN, is the common method of authentication. In theory, something you know will only ever be known to you, making it an effective method for verifying your identity. However, in reality, this is often not the case. Many users reuse passwords, use passwords that are easy to guess, or passwords that have already been leaked in a data breach, making it easy for attackers to gain access to their accounts. Furthermore, users can be tricked into giving up their secrets using phishing or other forms of social engineering attacks. As a result, relying solely on something you know for authentication is not recommended. However, it can be used in combination with other authentication factors to provide an additional layer of security. By using a combination of authentication methods, an attacker would need to have access to both the password and another factor such as a physical token or biometric data, making it much harder to gain access to a system.
For this reason, NIST defines in its Digital Identity Guidelines:
When a combination of two single-factor authenticators is used, it SHALL include a Memorized Secret authenticator (Section 5.1.1) and one possession-based (i.e., “something you have”) authenticator from the following list:
- Look-Up Secret (Section 5.1.2)
- Out-of-Band Device (Section 5.1.3)
- Single-Factor OTP Device (Section 5.1.4)
- Single-Factor Cryptographic Software (Section 5.1.6)
- Single-Factor Cryptographic Device (Section 5.1.7)
Somewhere you are or something you do
In addition to the three main types of authentication factors - something you are, something you have, and something you know - there are also other factors such as somewhere you are and something you do. Somewhere you are is location-based authentication, while something you do refers to behavioral biometrics, such as typing rhythm or mouse movement. However, these methods are rarely mentioned in scientific computer research, as they are relatively easy to spoof and have low confidence scores. For instance, location-based authentication can be spoofed using VPNs or proxies, while behavioral biometrics can be influenced by factors such as stress, alcohol, or medication. While these factors may offer some additional level of security, they are not considered reliable enough for most high-security applications. As a result, they are not widely used in authentication methods and are not recommended for use in high-security environments.
Industry-standard authenticators
The software industry has developed various authenticators to improve security and authentication methods. In the following sections, we will explore some of the most commonly used authenticators, including their benefits and drawbacks. By understanding these methods, you can choose the ones that best fit your needs and help to secure your users’ data.
Passwords
Passwords have a bad reputation because humans are not good at keeping secrets and remembering complex things accurately. Passwords can be guessed or a victim of social engineering, too long, too short, not complex enough, or simply reused across multiple accounts. As a result, attackers can use brute-force attacks, phishing scams, and other methods to gain access to user accounts. Furthermore, even when passwords are strong and complex, users can still forget them or store them insecurely, leaving them vulnerable to attack. To address these issues, best practices for password management should be followed, including using strong, unique passwords, regularly updating them, and using multi-factor authentication.
Despite their drawbacks, passwords are likely to remain a necessary part of our online lives for the foreseeable future due to the drawbacks of other authentication methods. While other methods such as something you have and something you are can provide a higher level of security, they also come with drawbacks that passwords do not have. Biometric authentication can be affected by factors such as physical injury, age, and environmental conditions, while physical tokens such as smart cards can be lost or stolen.
Password summary
- Attackers had 30 years to perfect attack vectors against passwords and are pretty good at it.
- Something you know and thus passwords will not be replaced as a security factor in the near-term.
- Passwords are a good fit for multi-factor authentication.
PIN Codes
PIN codes are commonly used for debit or credit cards and on mobile phones. These codes are typically 4-8 digits and can be user-chosen or generated by the system. While PIN codes provide a convenient method of authentication, they are vulnerable to brute-force attacks, where an attacker tries all possible combinations until the correct code is found. To mitigate this risk, many systems lock the account, device, or credit card after a certain number of incorrect attempts. However, in online systems, this can be problematic as attackers can effectively perform a denial-of-service attack on a user by trying to sign in too often with the wrong PIN.
Many mobile devices also have similar security measures, where the device is locked for a certain period if an incorrect PIN is entered too many times.
PIN code summary
- Vulnerable to denial-of-service and brute-force attacks.
- PIN codes are a convenient authentication factor.
- PIN codes are not a good fit for first-factor authentication in online systems.
Recovery codes
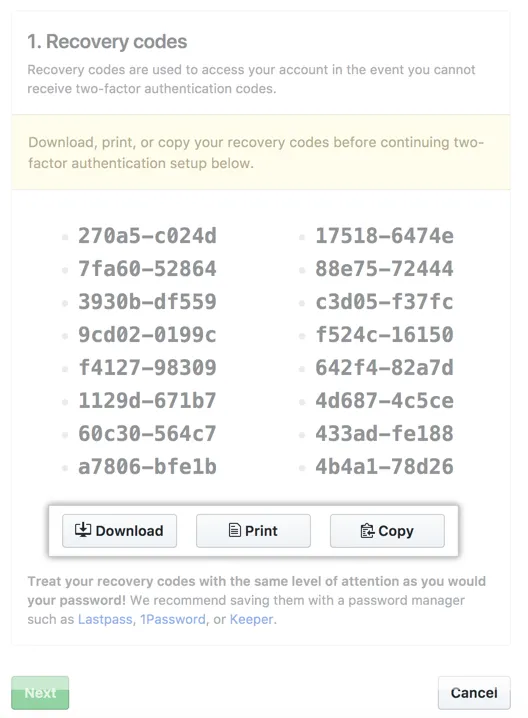
Recovery codes, something you have, also known as lookup secrets, are a type of authentication method used in 2FA systems. These codes are generated by the authentication system during the initial setup process and are used as a backup method for account recovery in case the primary authentication method is unavailable. Recovery codes are typically a set of random numbers or characters that are provided to the user during the setup process and can be used exactly once to access the account in the event of a lost or stolen device, or other authentication issues.
Recovery codes should be kept secure and should only be provided to the authorized account owner to prevent account hijacking or unauthorized access.
Recovery code summary
- Attackers can steal recovery codes, and they need to be kept in a very safe space, outside of the password manager.
- Recovery Codes are similar to PIN codes but for one-time use.
- Recovery Codes are used as a backup or recovery mechanism when the primary second factor is lost.
Magic link via email
Magic links via email have gained popularity in recent years as an alternative to traditional passwords. This method falls in the something you have spectrum, as users need access to the email account associated with their online account to complete the login flow.
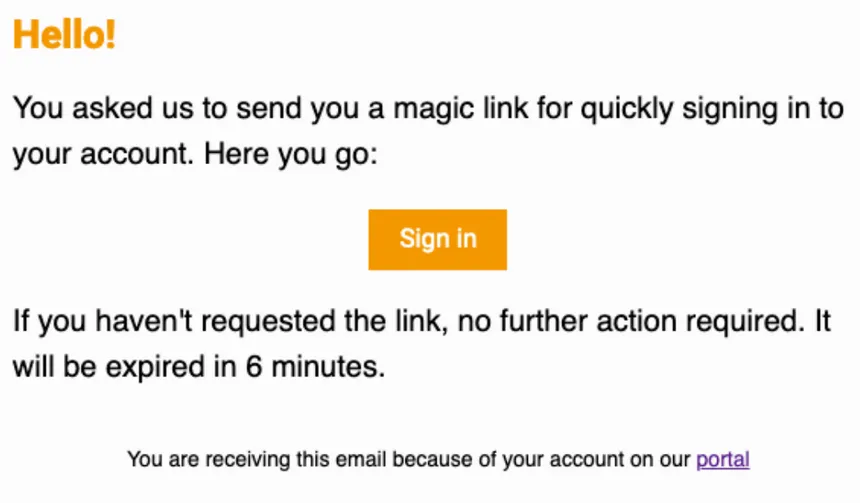
Since most account recovery mechanisms rely on proof that the user has access to the recovery address (using the right password), they typically do not reduce the level of security compared to passwords significantly. However, magic links have several problems that can make them unreliable for authentication. For example, email delivery is not always immediate or can fail, which can leave users stuck trying to complete the login flow.
Additionally, magic links open in a browser, which can cause issues such as opening the link in the wrong browser, malware scanners invalidating the link, and the login process failing when initiated on one device and completed on another. While magic links can be a convenient and simple way to authenticate users, they are not without their drawbacks and may not be suitable for all use cases.
If you want to use email for authentication, a login code via email is a more reliable and secure method, as it eliminates some of the problems associated with magic links.
Magic link via email summary
- Magic links are a convenient way of onboarding - only the user’s email is needed
- Magic links have issues when being used cross-device or cross-browser and don’t work well on mobile apps; email delivery can be unreliable, causing a bad user experience
- Use login code via email instead.
Login code via email
Login code via email is a method of authentication that sends a verification code to the user's email, which they then enter on the page where the login flow was initiated. This method can be more reliable and secure than magic links, as it eliminates some of the browser-related issues and works well on mobile. However, the same limitations around email deliverability apply, and users may be unable to receive the verification code on time or at all. Therefore, it is important to ensure that alternative authentication methods are available and that users are aware of the potential limitations and issues associated with email-based authentication.
Login code via email summary
- Login codes are convenient when onboarding new users.
- Prefer this method over magic links.
- Same email deliverability and user experience issues as magic links via email.
- Can be used as a fallback mechanism for passwordless login using Passkeys / Biometrics or when not having access to the password manager.
Login code via SMS
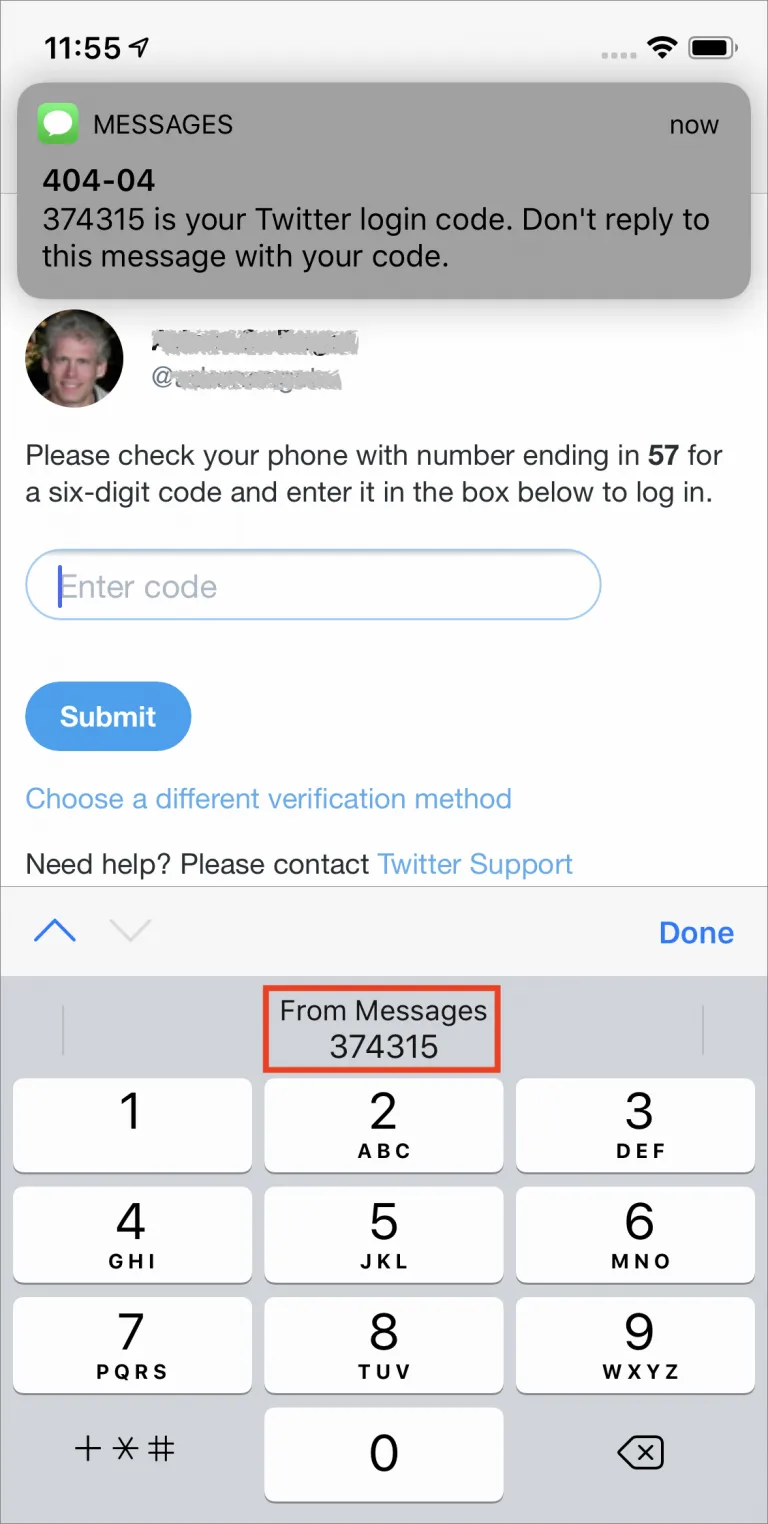
Login code via SMS is another method of authentication that has been used in the past. However, this method is now banned in many government agencies and enterprises due to its security vulnerabilities. In many parts of the world, SMS sending and receiving is based on old protocols that are easy to spoof, eavesdrop on, or reroute. Attackers can intercept SMS messages or even clone SIM cards, allowing them to gain access to user accounts. Additionally, users may not receive the SMS code on time, or the SMS message may be intercepted or delayed due to network issues. As a result, SMS-based authentication is not considered a secure method of authentication and is no longer recommended by many security experts. It is important to use alternative authentication methods that provide a higher level of security and protection against cyber attacks.
For more information on the vulnerabilities see “A Hacker Got All My Texts for $16” by Joseph Cox (Journalist, Motherboard) and “It's Time to Hang Up on Phone Transports for Authentication” by Alex Weinert (Microsoft Identity Division). Providing a full list of SIM-related security incidents is too long to include in this article, but here are three recent high-profile incidents:
- The frighteningly simple technique that hijacked Jack Dorsey’s Twitter account
- U.S. cryptocurrency investor sues suburban NYC teen for $71.4 million over alleged swindle
- FBI Received 1,600 SIM Swapping Complaints in 2021
Login code via SMS summary
- Attackers can find many cheap and simple ways to gain access to the login codes.
- Login code via SMS is very convenient for users with mobile devices.
- Default to not using SMS-based authentication.
Authors note: The decision by Apple to make this method even more convenient was a poor decision security-wise.
TOTP / Google Authenticator

Time-based One-Time Password (TOTP) is a common form of authentication, something you have, that involves generating a one-time code that is valid for a short period (typically 30 seconds) using a shared secret and the current time. This code is generated by an authentication app such as Google Authenticator and is entered along with the user's password to complete the authentication process. TOTP can be an effective method of authentication as it provides an additional layer of security beyond the password. Additionally, TOTP can be stored in password managers for added convenience, though this presents a security risk if the password manager is compromised. TOTP does not require an internet connection or mobile network coverage, which can be useful in areas with limited connectivity. However, one drawback of TOTP is that the user must have access to the device where the authentication app is installed to generate the code. Additionally, if the shared secret is compromised, the TOTP code can be easily generated by the attacker.
TOTP / Google Authenticator summary
- The device can be lost, stolen, or broken.
- TOTP is considered two-step verification when stored in the same vault (password manager) as the password.
- TOTP has a good balance between usability and security for second-factor authentication when used together with passwords.
Passkeys, FaceID, Windows Hello: WebAuthn
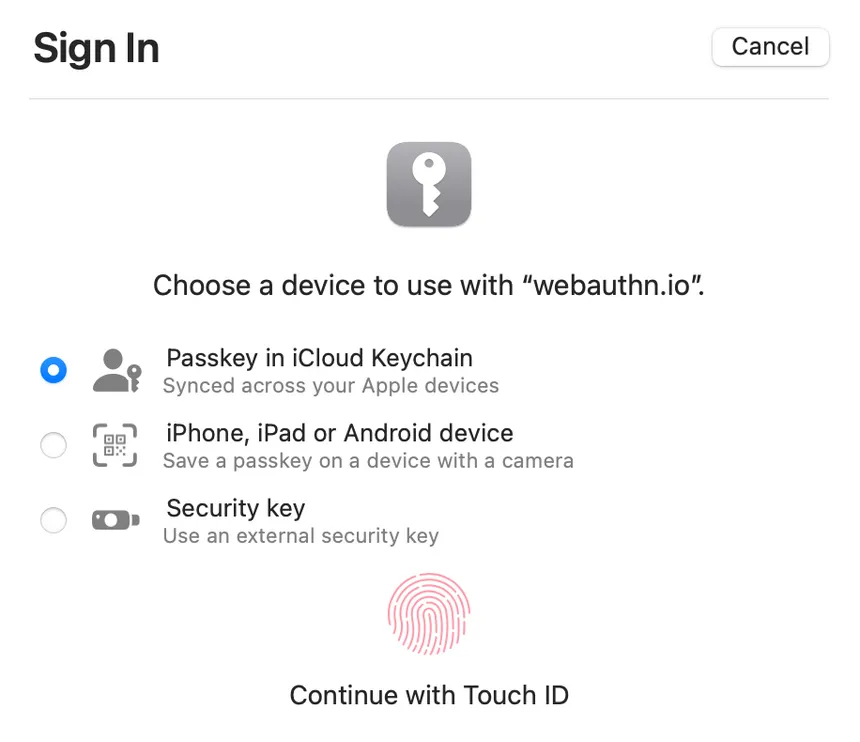
WebAuthn is a web standard for passwordless authentication that was developed by the World Wide Web Consortium (W3C) and the FIDO Alliance and is the best contender to become the common authentication method on the internet. It allows users to log in to websites and applications using biometric factors, security keys, or other devices, without the need for a traditional password. WebAuthn is designed to be secure, private, and easy to use, and it is supported by many browsers and platforms. By eliminating the need for passwords, WebAuthn can significantly reduce risk.
WebAuthn is a JavaScript SDK that is built into modern browsers, including Chrome, Firefox, Safari, and Microsoft Edge:
// Example
const credential = await navigator.credentials.create({
publicKey: publicKeyCredentialCreationOptions,
})
This means that website developers can use WebAuthn to implement passwordless authentication without requiring users to install any additional software or browser extensions. By using the browser’s built-in security features, WebAuthn can be a secure and convenient authentication experience for users.
Authenticators compatible with WebAuthn include:
- Apple FaceID and Apple TouchID
- YubiKeys
- Passkeys
Platform versus Cross-Platform
WebAuthn has two distinct modes of operation, platform mode, and cross-platform mode.
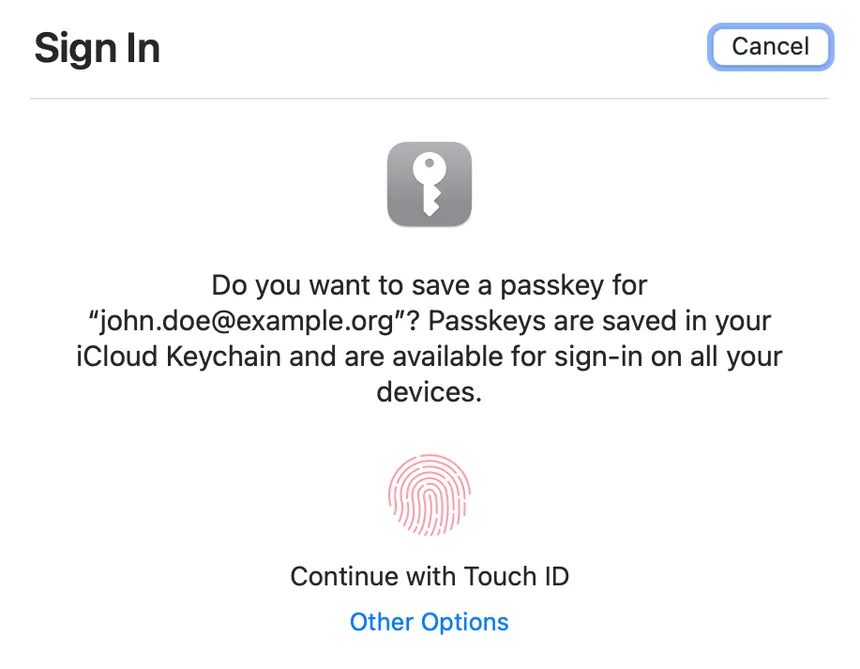
Platform mode uses authenticators that are integrated into the client device or platform, such as a TPM (Trusted Platform Module) or a built-in fingerprint scanner. These authenticators are often referred to as "built-in" or "on-board" authenticators because they are integrated into the device’s hardware or firmware. In platform mode, the authenticator communicates directly with the browser to perform the authentication process, and the private keys are stored securely on the device.
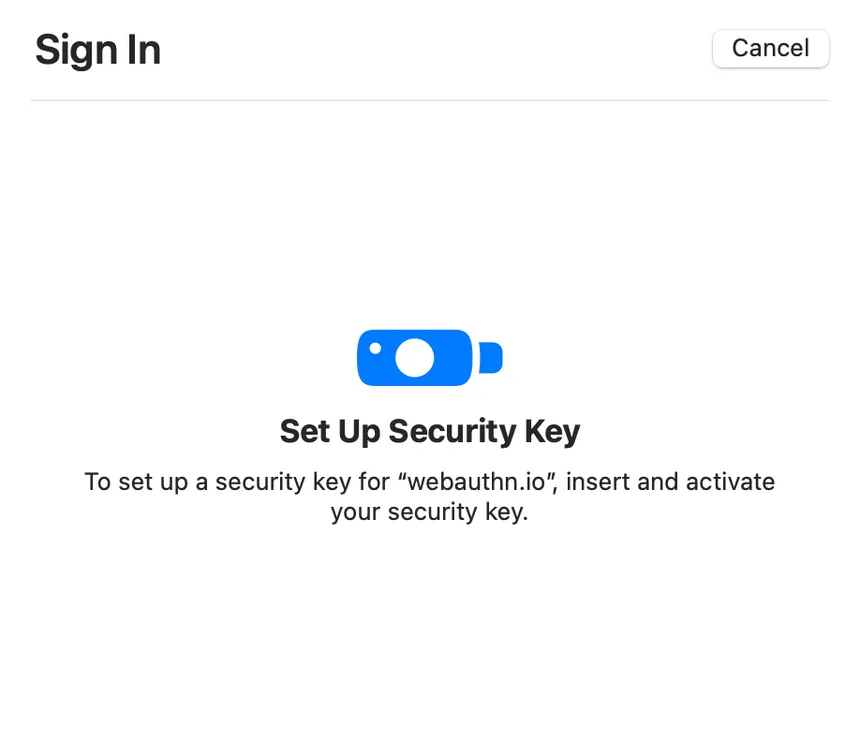
Cross-platform mode, on the other hand, uses external authenticators that can be connected to a device via USB, NFC, or Bluetooth. These external authenticators are often referred to as "roaming" or "portable" authenticators because they can be used with multiple devices. In cross-platform mode, the authenticator communicates with the browser through a client device or a cloud service, and the private keys are stored on the external authenticator.
Platform biometrics are only as strong as your system password
It's important to note that TouchID, FaceID, Windows Hello, and other platform mechanisms are used to unlock the system "keychain" where all the credentials are stored. While these authentication methods are typically categorized as something you are factors, in reality, they are used to authenticate the user to the operating system, rather than to a specific website or application. When the user's biometric data is not recognized, the operating system falls back to using a password: something you are is now something you know.
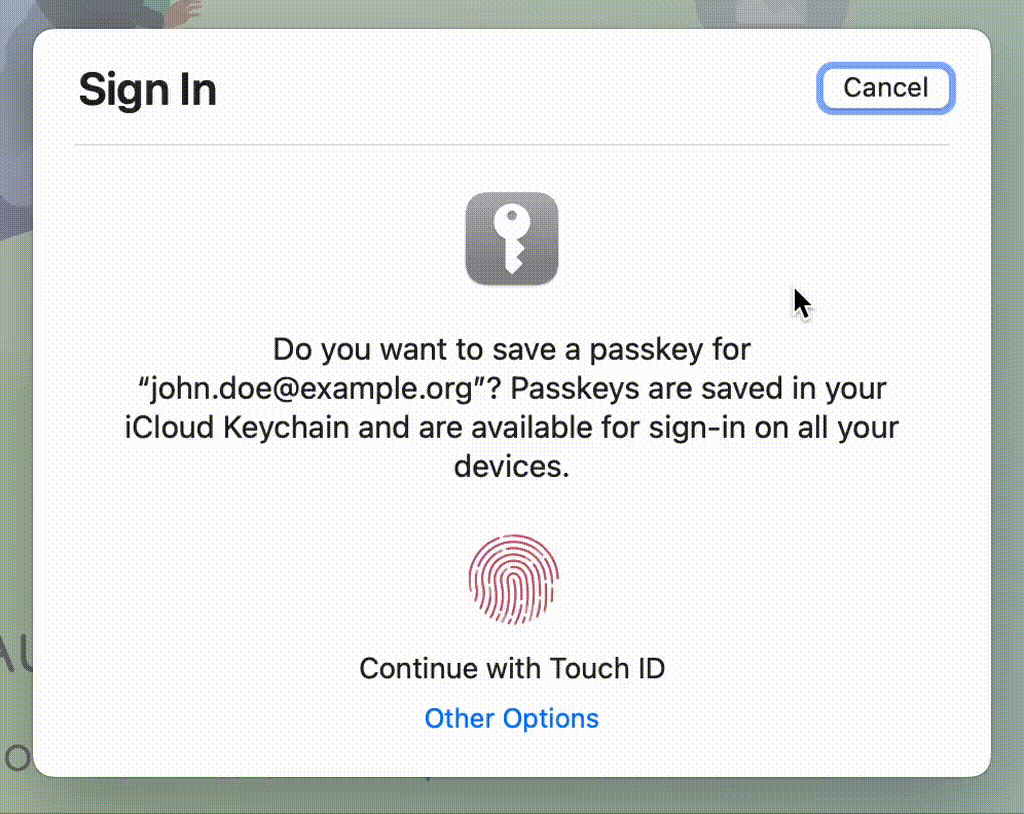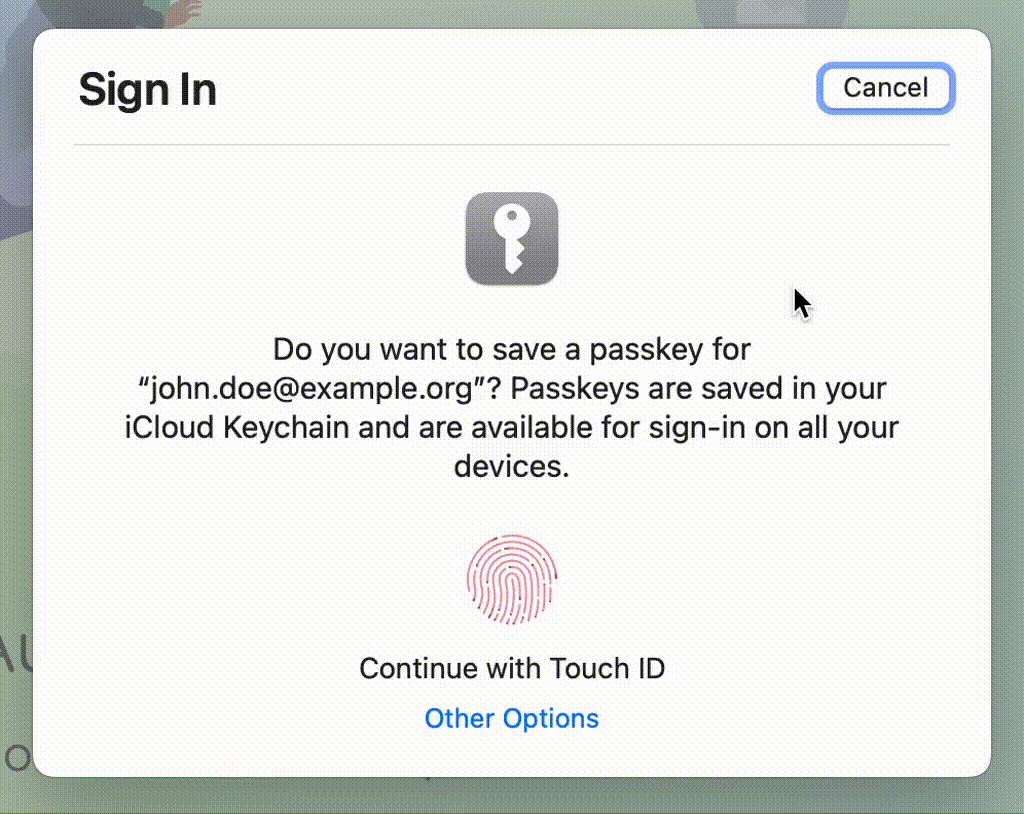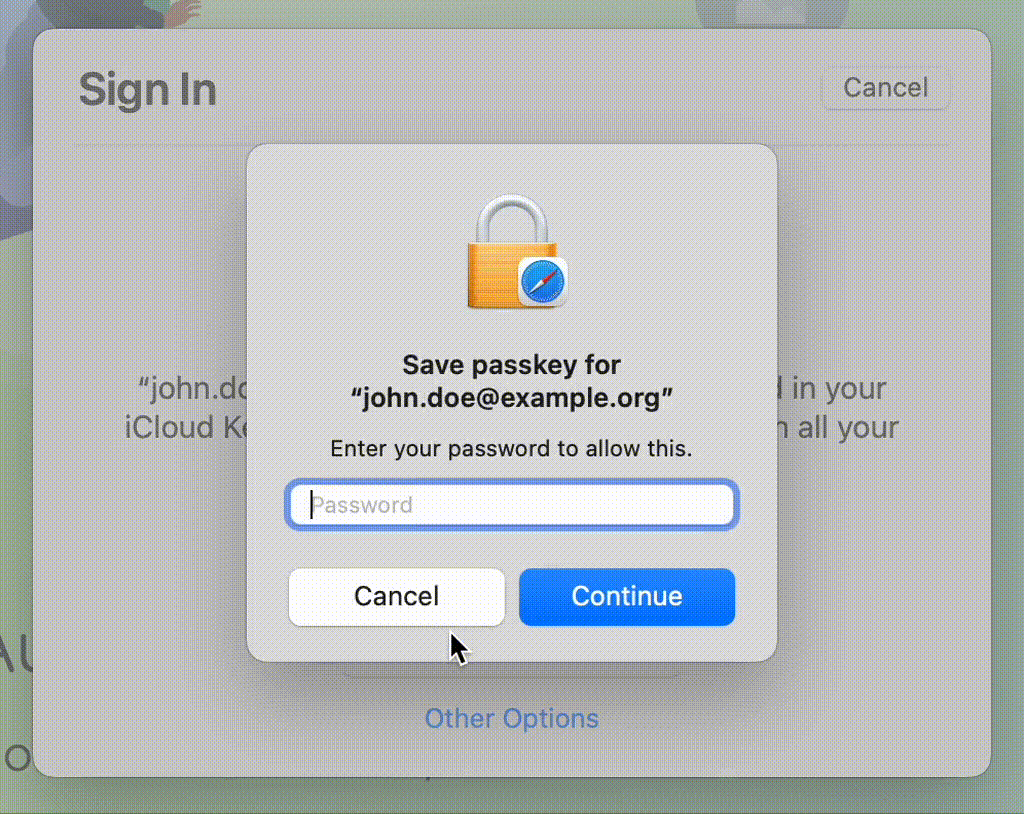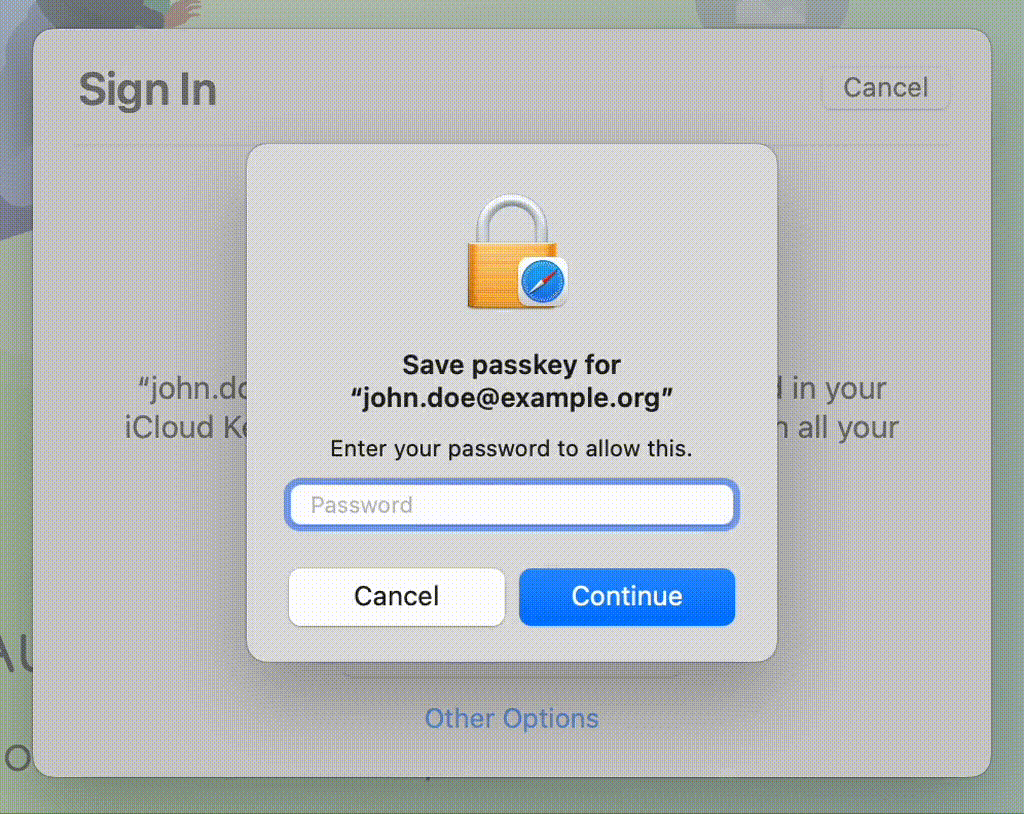
This is an important distinction because it means that the security of the stored credentials depends not only on the strength of the biometric authentication method but also on the strength of the password used to protect the keychain. Additionally, since the keychain is only unlocked when the user is logged in to the operating system, this authentication method may not be suitable for scenarios where the user needs to authenticate to a website or application without being logged in to the operating system.
YubiKeys are pretty good security

YubiKeys are a popular hardware token used for two-factor authentication. YubiKeys come in different variations, but they all provide a physical key that generates a one-time password that is used to authenticate the user. The YubiKey 5 series, for example, delivers proof of possession. If a PIN code is configured and the WebAuthn relying party (the website) requests user verification, proof of knowledge can be presented as well.

Other Yubikeys such as the Bio series have built-in fingerprint sensors that support two-factor authentication in one device. With the YubiKey Bio, the user must provide both something they have, the physical key, and something they are, their fingerprint, to authenticate. This provides a higher level of security than using a YubiKey without user verification, as it helps to prevent unauthorized use of the key by an attacker who has stolen it.
Cross-Platform Passkeys
Passkeys support cross-platform WebAuthn as well. By storing the cryptographic key on a separate device or ecosystem (Android / Apple), the user can authenticate themselves across multiple devices and platforms using the same key. This can be a convenient and secure way to authenticate, as it allows the user to leverage the security features of different devices and ecosystems.
For example, a user might generate a cryptographic key on their Android phone and then use that key to authenticate themselves on an Apple device using WebAuthn.
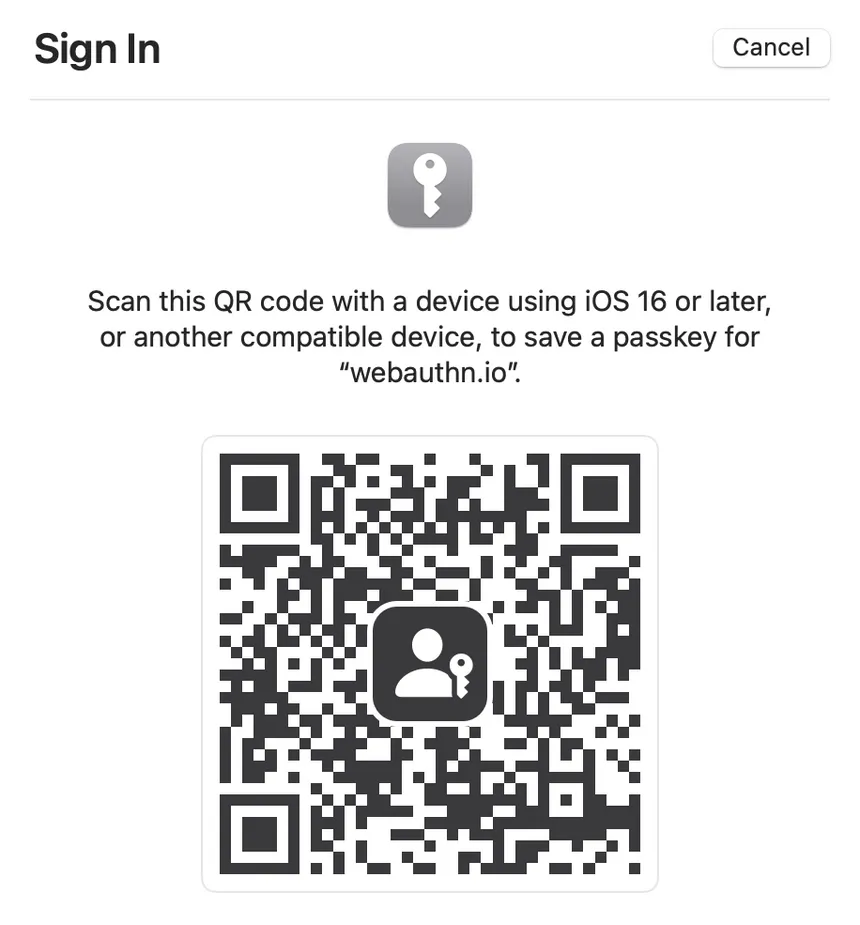
The strength of the authentication is similar to using a fingerprint to unlock the keychain, as both methods rely on the user's possession of a trusted device to prove their identity.
WebAuthn lacks control over the authenticator
The WebAuthn API provides limited control over the authentication method used, as the platform and device being used ultimately determine which factors of authentication are requested from the user. While it is possible to extract some metadata about the transport used and the basic information about the type of credential used, it can be difficult to get detailed metadata about the specific authentication process and the factors used.
This lack of control over the authentication mechanisms used can be a potential weakness in some scenarios, as it means that the relying party has less control over the security of the authentication process. For example, if the relying party requires the use of biometrics for authentication, but the device being used is unable to provide biometric data, the user may be able to authenticate using a less secure method, such as a PIN or password.
WebAuthn is not multi-domain capable
WebAuthn credentials are bound to a specific domain and cannot be shared with
other domains. This can make it difficult to use WebAuthn in scenarios where
users need to authenticate across multiple domains or when a domain change is
necessary, such as when a website moves from one domain to another (from
example.org to example.net). The problem arises because the cryptographic
key that is used for WebAuthn authentication is tied to the domain, so a key
generated for one domain cannot be used for another.
Read more about this problem in the GitHub issue w3c/webauthn#1372.
WebAuthn summary
- WebAuthn is phishing resistant because it is bound to hostnames.
- WebAuthn is a major improvement in security and convenience.
- WebAuthn lacks control and metadata for top security environments.
- WebAuthn does not support sharing keys across domains.
QR code
This method involves generating a unique QR code that is displayed on the login screen, which the user scans using a mobile device. The device then sends a token to the server to complete the authentication process.
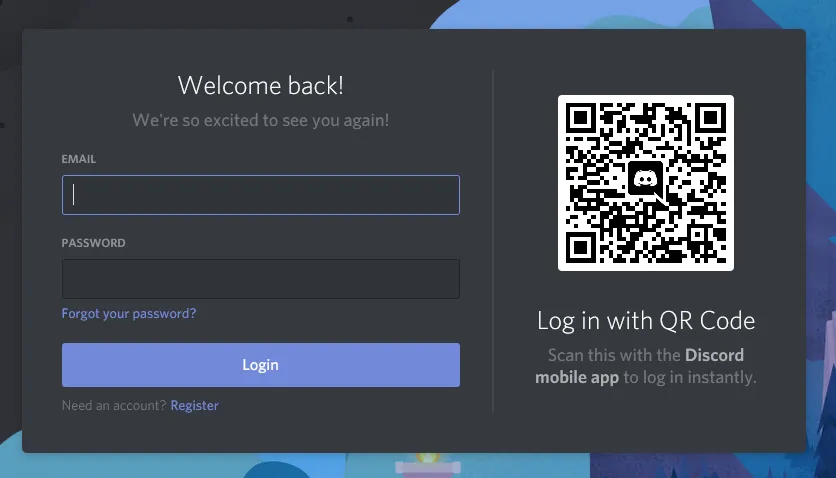
However, like all authentication mechanisms, Login via QR code has its drawbacks. One of the main concerns is that it requires users to have access to a mobile device, which is not always convenient or practical. Additionally, the process can be time-consuming and may not be suitable for high-volume transactions.
Finally, this method should always be used as a complementary authentication mechanism, and not as the sole method of authentication. A fallback login method, such as username and password, should always be available to users in case they are unable to use the QR code authentication method.
In summary:
- QR codes can offer some convenience if the device is available and the app is installed.
- Requires complementary authentication method (for example username and password) as a fallback.
- Use WebAuthn with QR code instead.
Social Sign-In / Single Sign On
Social sign-in and single sign-on (SSO) are two related methods of authentication that have gained popularity in recent years due to their convenience and ease of use. Social sign-in allows users to authenticate using their social media accounts, such as Facebook or Google, without having to create a separate account. SSO allows users to authenticate across multiple systems or applications using a single set of credentials, making it easier to access different services without having to remember multiple login details. Additionally, these methods can enhance the user experience by simplifying the login process and reducing the time and effort required to access online services.
However, users should be aware of the privacy implications of these methods and should be given the option to opt out of data sharing where possible. Additionally, social sign-in providers usually do not expose multi-factor controls. This has three implications:
- Social sign-in may have privacy implications and lock-in with vendors
- It is convenient and secure
- Still needs an extra second factor for multi-factor authentication
Security Questions
Security questions were a popular method of authentication in the past, but they have fallen out of favor due to their vulnerability to social engineering attacks. In particular, the iCloud celebrity leak, where hackers gained access to celebrities' accounts by correctly guessing their security questions, highlighted the weaknesses of this method.
Security questions are often based on personal information that can be easily found or guessed, making them vulnerable to brute-force attacks. Additionally, security questions can be subject to biases and can be difficult to remember or answer accurately, leading to account lockouts or password resets. While security questions may still be used in some systems, they are no longer considered a secure method of authentication and should be avoided where possible.
In summary
- don’t use security questions
Password managers
Password managers are an interesting phenomenon that has emerged in response to the challenges of password management. Since humans are bad at remembering complex sequences, we have invented a vault full of passwords that we don't know, because we "unlock" them with a main password. This raises an interesting question of whether using a password manager changes what passwords are from something you know to something you have which I do not have an answer to.
Furthermore, password managers support storing additional factors such as TOTP codes or recovery codes for added convenience. While this can be useful for users, it also presents a security risk, as all the authentication information is stored in one place. If the password manager is ever compromised, or the master password is leaked, the user's entire authentication profile could be at risk. This has happened very recently, as LastPass was hacked and vault data stolen due to dated cryptography settings. This may spell trouble for many soon. Password managers are also susceptible to phishing attacks, like any other password-protected authentication.
A tale of two steps
In some cases, an authentication process involves two steps but not two factors.
- Two-step verification (2SV) is a type of authentication that uses two factors of authentication.
- Two-factor authentication (2FA), on the other hand, is a type of authentication that uses two distinct factors of authentication.
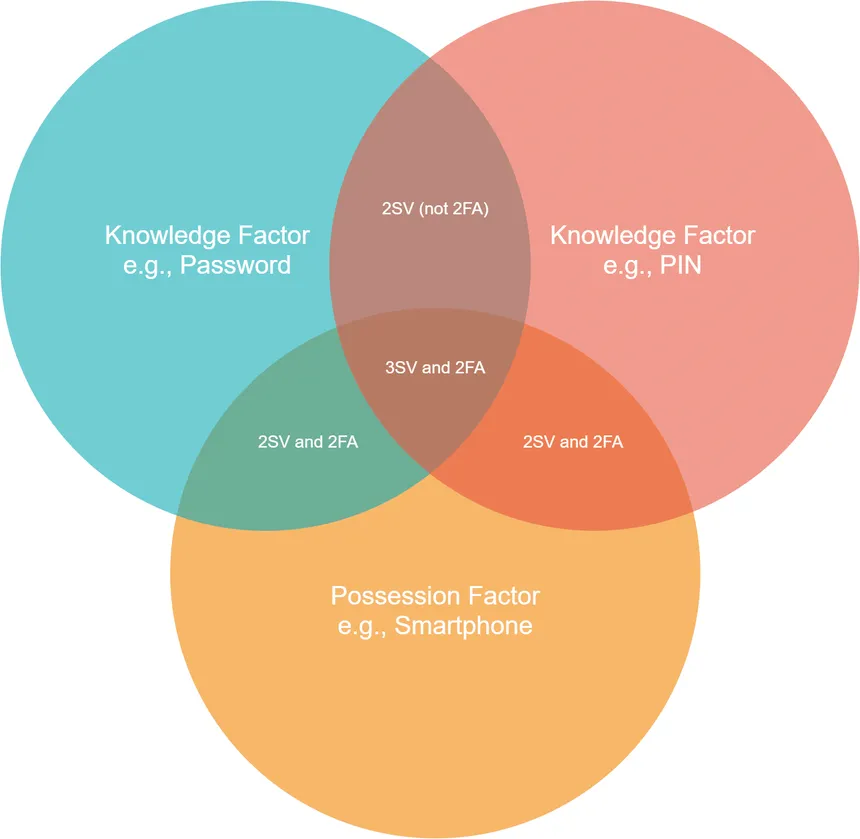
An example of two-step authentication that is not two-factor authentication is the combination of a password and the email link authentication method. The email link authentication method requires the user to click on a link sent to their email address to verify their identity. Since the link is sent to something the user knows, namely their email account, it is an example of something you know. In this case, the user must provide a password and then click on the link sent to their email, which is two-step authentication but not two-factor authentication, as it relies on two instances of something you know rather than two distinct factors of authentication.
Similarly, a passwordless login that requires two separate WebAuthn security keys is 2SV but not 2FA.
Account recovery
Account recovery is an essential aspect of authentication that allows users to regain access to their accounts if they forget their password or if their account is compromised. The most common method of account recovery is to send a magic link or verification code to the user's email address. While this method can be convenient and effective, it may present a weak spot in your authentication model. Security questions or verification codes via SMS are no longer considered secure methods of authentication and should be avoided where possible.
Account recovery with a second factor typically involves lookup secrets or recovery codes that can be used to reset the account password or regain access to the account. These codes should be kept secure and should only be provided to the authorized account owner to prevent account hijacking or unauthorized access. Users should always have at least two distinct second-factor authenticators (two security keys, TOTP + FaceID, …) but also be aware that the authentication security is only as strong as the “weakest” second factor.
What does Ory recommend?
Ory is an open-source identity and access management solution that provides a flexible and secure authentication framework for modern applications. With Ory, businesses can implement a range of authentication mechanisms to suit their specific needs, including common factor authenticators like passwords, WebAuthn, social sign-in, single sign-on, and lookup secrets.
One of the key benefits of Ory is that it provides full control over advanced authentication flows like WebAuthn, allowing businesses to customize their authentication mechanisms to their specific threat model and security requirements. For example, businesses can choose between different levels of security, such as two-step verification, passwordless authentication, or two-factor authentication, depending on their security needs.
Ory does not implement insecure authentication mechanisms like security questions, which are vulnerable to social engineering attacks and have been associated with high-profile security breaches in the past.
Conclusion
In conclusion, authentication is a critical part of securing online systems and protecting user data. While passwords remain the most common form of authentication, they have well-known limitations and are vulnerable to various types of attacks. As a result, businesses and developers are increasingly turning to other authentication methods, such as something you have, and something you are.
In this article, we have discussed a range of authentication mechanisms, including password managers, PIN codes, magic links, TOTP, YubiKeys, and WebAuthn. We have highlighted the benefits and drawbacks of each of these methods and explained how they can be used effectively in different contexts.
Ultimately, the best authentication method for a given situation will depend on the specific security requirements and threat model of the business or application in question. It is important to be mindful of the trade-offs between security, convenience, and usability, for each authentication mechanism and choose one that balances these factors effectively.
One effective solution for managing authentication in modern applications is Ory, which provides a flexible and secure authentication framework that can be customized to meet the specific needs of any business. With Ory, businesses can implement a range of authentication mechanisms, including common factor authenticators like passwords, WebAuthn, social sign-in, single sign-on, and lookup secrets, while avoiding insecure mechanisms like security questions.
Sources
- Something You Know, Have, or Are
- Authentication using the Public Switched Telephone Network
- It's Time to Hang Up on Phone Transports for Authentication
- A Tale of Two Errors: Measuring Biometric Algorithms
- 1Password and time-based one-time passwords
- What’s the Difference Between 2FA and 2SV?
- Web Authentication: An API for accessing Public Key Credentials Level 2
Further reading

The future of Identity: How Ory and Cockroach Labs are building infrastructure for agentic AI

Ory and Cockroach Labs announce partnership to deliver the distributed identity and access management infrastructure required for modern identity needs and securing AI agents at global scale.

Ory + MCP: How to secure your MCP servers with OAuth2.1

Learn how to implement secure MCP servers with Ory and OAuth 2.1 in this step-by-step guide. Protect your AI agents against unauthorized access while enabling standardized interactions.